In the past month, it has been widely publicised the damage that the ransom-ware WannaCry has caused to businesses both large and small throughout the world. Australia was lucky with the timing of this ransomware – it was released on a Friday night Australian time, meaning that by the time everyone woke up on Saturday, a solution was already in place, minimising the impact.
WannaCry could have been much worse
Many people and businesses are still using outdated, unpatched Windows XP and Windows 7 machines which allow for these exploits to take down your computer network. Even Windows 8 and 10 can be vulnerable if they are not kept up to date.
WannaCry ended up affecting over 250,000 computers in 150 different countries.
Since the initial outbreak, there has been several spin-offs from the original. The main threat currently is pop-ups appearing in web browsers that tell the user their machine has been affected by WannaCry. The pop-ups instruct the user to call an ‘assistance team’ number, where they are told to download software to give the ‘assistance team’ remote access to the computer. Once remote access is given, the computer is severely compromised.
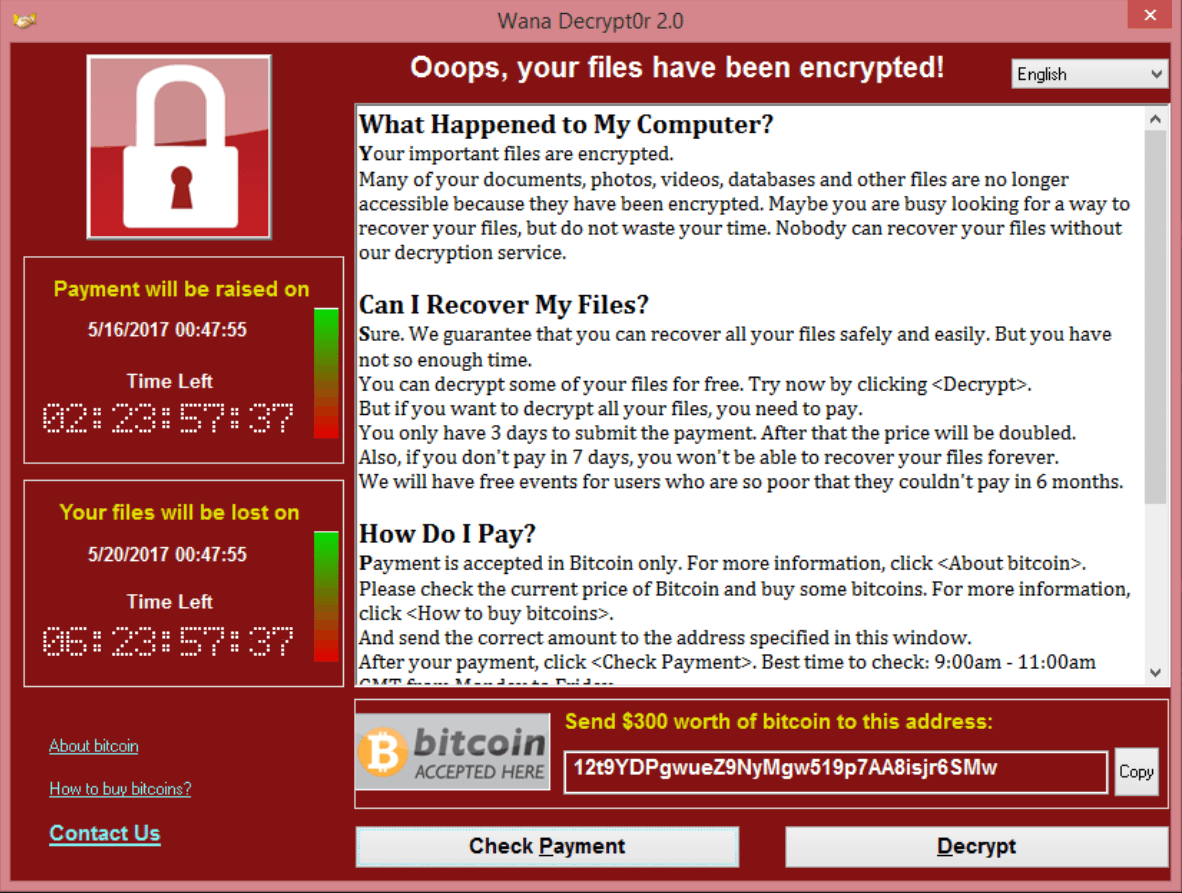
Steps to reduce risk of WannaCry
We have written in the past about the simple steps each business can take to protect themselves from a cyber-attack. As a refresher, the Australian Government uses the terminology ‘The Essential Eight’ when it comes to protecting a network. These eight strategies are:
- Patch / Update operating systems (ie, Windows)
- Patch / Update applications (ie, Office 365)
- Restrict Administration Privileges
- Whitelist Applications – Only allow certain applications to run
- Block web browser access to Adobe Flash, web ads and untrusted Java code
- Disable un-trusted Microsoft Office macros
- Enable Multi-Factor Authentication where possible (banking, emails etc)
- Daily backup of all important data
You can read more about the government strategy for businesses here.
To read more about Cyber Risk Management including Cyber Insurance, please visit the following information pages:




Comments are closed.